Today, almost 63% of the global population uses the internet, making it even more important for electronic devices to be safe and secure. The world is well connected due to the advent of the Internet of Things (IoT), which has completely transformed our interactions.
The security vulnerabilities of increased internet connectivity are just as real as pollution, which was a side effect of the Industrial Revolution. Cyber attacks aggressively exploit these vulnerabilities.
Hackers and scammers have started coming up with ways to gain unauthorized access, data breaches, and possible compromises of personal or sensitive information. To fight against these cybercrimes, both individuals and organizations must be aware of these threats and adopt a thorough strategy to defend against them. As we look into 2024, let’s explore the top cybersecurity threats and how to protect data against them.
What is Cybersecurity?
In simple terms, cybersecurity is protecting computers, computer networks, mobile devices, various electronic systems, communications, and data from malicious attacks. It is also known as information technology security, electronic information security, or simply IT security.
Current Cybersecurity Landscape
According to a shocking report by Cybersecurity Ventures, the cost of cybercrime reached $8 trillion in 2023, which means over $250,000 per second—a considerable amount of money, right? The alarming situation is that the amount is expected to rise to $10.5 trillion by 2025.
This immense financial impact highlights the critical need for organizations across industries to be prepared against evolving threats, ensuring resilience and security. Current cyber security threats involving malware, phishing, machine learning, artificial intelligence, and cryptocurrency place the data and assets of corporations, governments, and individuals at constant risk. The shortage of cybersecurity professionals also worsens the situation, making the stakes higher than ever.
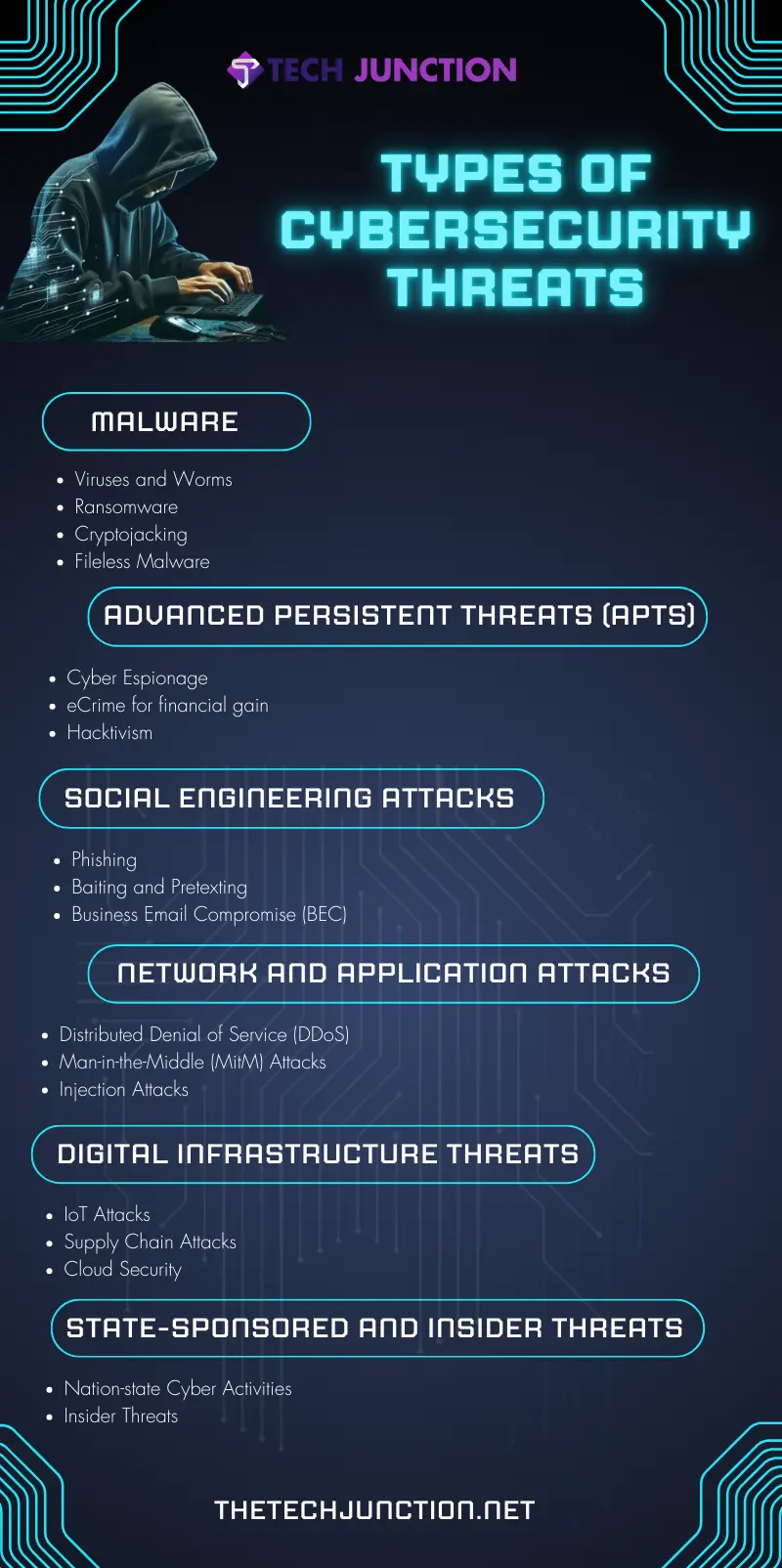
Types of Cybersecurity Threats
As digital landscapes evolve and advance, so do the types of cyber threats that target them. There are so many types of it, and each year, there is an addition of these threats; as security advances, the scammers also find some loophole to attack.
These security threats can be broadly categorized into several types, each with unique characteristics and methodologies:
1. Human Risks
The biggest risk in cybersecurity is often not the technology itself but the people who use it, who are considered the weakest link. Human risk is regarded as a top cybersecurity threat because humans play a central role in organizations’ operational and security processes.
The most common human risks involve careless behaviors at the workplace, such as using weak or reused passwords, failing to secure physical devices, mishandling sensitive information, or downloading malicious software by mistake. Poor security hygiene and insider credential theft can leave organizations vulnerable to exploits and attacks. People don’t read the terms and conditions of software and websites, so there is always a chance that a person can unintentionally give way to scammers by giving permission.
A recent study by the security firm Mimecast found that human errors are the biggest cyber security risks for businesses. The report highlights that in 2023, over 70% of cyber breaches were caused by mistakes made by people. These included incidents where credentials were stolen, identities were compromised, social engineering tactics were employed, and access privileges were misused.
2. Malware Threats
Malware continues to evolve, becoming more complex and stealthy, making detection and mitigation challenging. Due to its wide range, financial impacts, and potential for data thefts, it is considered one of the biggest cyber threats.
Some top malware threats include viruses, worms, ransomware, crypto-jacking, and file-less malware.
3. Viruses and Worms
Though some of the oldest types of malware, viruses, and worms are still effective, viruses attach themselves to clean files and spread, causing damage. Worms can replicate themselves and spread through network vulnerabilities without human help.
4. Ransomware
Ransomware is increasing in 2024. Hackers usually attack the education sector, healthcare institutions, and the finance sector. Ransomware attacks involve encrypting the victim’s data and demanding payment for decryption.
They can paralyze critical systems and require a large amount of money to resolve. Ransomware as a Service (RaaS) has made it easier for criminals to launch these attacks more frequently.
5. Cryptojacking
As we all know, digital currency is in demand, and crypto-jacking uses your computer’s resources to mine cryptocurrency without your knowledge, slowing down your system.
6. Fileless Malware
This malware doesn’t use files to execute its attack. Instead, it utilizes legitimate programs to carry out its harmful activities, making it harder for traditional antivirus programs to spot.
7. Social Engineering Attacks
Social engineering uses human interactions to gain unauthorized access to critical information and systems. Phishing is one of the most common examples, where attackers try to fool users into sharing personal details, login information, or OTP.
8. Phishing
Phishing is one of the most used cyber attacks. Attackers trick people into giving up sensitive and personal information. Through this method, they try to access personal information like login credentials, debit or credit card details, and other bank-related information by pretending to be concerned company authorities.
Variants like spear phishing(targeted attacks), vishing (voice phishing), and smishing (SMS phishing) are becoming more sophisticated and complex to detect.
9. Baiting and Pretexting
We all are frustrated by spam calls and receive fake offers and lotteries, usually from scammers. Baiting involves enticing victims with promises of goods or information, while pretexting involves attackers pretending to be someone else to gather personal information.
10. Business Email Compromise (BEC
Almost all businesses revolve around emails, and scammers are taking advantage of this. Also, email addresses are easily accessible, and scammers use email fraud to trick companies into sending money or sensitive data to criminals.
Network and Application Attacks
These attacks target the core of IT infrastructures:
1. Distributed Denial of Service (DDoS)
DDoS attacks overload systems with internet traffic, disrupting services and acting as a distraction while more severe attacks are carried out in the background.
2. Man-in-the-Middle (MitM) Attacks
MitM attacks occur when someone secretly intercepts and potentially alters the communication between two parties or between a user and an application to steal or manipulate information. They often exploit SSL/TLS protocol flaws.
3. Injection Attacks
SQL injection, code injection, and OS command injection involve sending untrusted data to an interpreter, executing unintended commands, or accessing unauthorized data.
Digital Infrastructure Threats
As technology advances, new challenges arise in IoT, supply chains, and cloud computing:
1. IoT Attacks
IoT devices often lack robust security, making them easy targets. Once hacked, these devices can be used to create botnets for DDoS attacks.
2. Supply Chain Attacks
Supply chain attacks involve tampering with software or hardware before it reaches the consumer. Attackers exploit trusted relationships to sneak in harmful code or components.
3. Cloud Security
Misconfigurations in setting up cloud services or poor access controls can result in unauthorized access data breaches.
4. State-sponsored and Insider Threats
Due to technological advancements, the war between the two countries has also shifted towards online by using the internet, also called the Fifth Generation war in broader terms. These threats pose sophisticated challenges:
5. Nation-state Cyber Activities
These are attacks carried out by governments or their agents, often to spy, damage infrastructure, or influence political situations. They are usually very sophisticated and have long-term objectives.
6. Insider Threats
Insider threats arise from within an organization, like employees or contractors. These cyber threats can be accidental or intentional, and they are especially risky because they use legitimate access to get around regular security protections.
7. Advanced Persistent Threats (APTs)
APTs are complex, stealthy, and secretive attacks that target specific individuals or organizations to steal data or disrupt operations. They often stay hidden for long periods.
8. Characteristics of APTs
They involve highly targeted, long-term engagements using advanced malware and evasion techniques. Once access is gained, APTs move laterally through networks, establishing footholds in different parts of an organization’s digital infrastructure.
Mitigation Strategies: How to Protect Against Cybersecurity Threats
Below are some strategies and considerations to help you protect against these threats in 2024. By implementing these measures, you can strengthen your defenses and reduce the risk of cyber attacks.
1. Defending Against Malware Threats
To combat malware threats, organizations should adopt a layered security approach. This measure includes regular software updates, comprehensive end-user education, advanced threat detection systems, and rigorous access controls.
Many software programs are available to detect attacks, and there should be a strict protocol that everybody must install such software to fight against these cybersecurity concerns. Having a solid cybersecurity plan and regularly checking for issues can make it easier to identify the problems early and keep your data safe.
2. Protecting Against Social Engineering Attacks
Organizations must prioritize security awareness training for their employees to recognize and respond effectively to social engineering attacks. To counter this issue, Implement multi-factor authentication (MFA), which can significantly reduce the risk of successful breaches from these tactics. Developing and rehearsing incident response plans ensures preparedness for potential breaches.
3. Safeguarding Network and Application Security
Comprehensive threat monitoring systems are essential for detecting and mitigating DDoS attacks before they cause significant damage. Proper SSL/TLS configurations and educating users on secure internet connections are vital for MitM attack prevention. Implementing rigorous input validation and preparing statements with parameterized queries can prevent injection attacks.
4. Enhancing Digital Infrastructure Security
Securing IoT devices requires regular firmware updates, default credential changes, and network segmentation. Continuous vetting of suppliers, adherence to strict security standards, and integrating security practices into contract agreements can enhance supply chain security. Cloud security can be strengthened by utilizing automated tools for configuration monitoring, rigorous access controls, and employee training.
5. Addressing State-Sponsored and Insider Threats
Cybersecurity threats are not limited to a particular country or region; they are everywhere. So, the world has to address them with cooperation. Strengthening national cybersecurity policies, enhancing international cooperation, and developing counter-cyber espionage strategies are critical for nation-state threats. Implementing behavioral analytics, access controls, regular audits, and continuous employee education on security policies is essential for insider threats.
6. Privacy and Data Breach Prevention
To address and counter this issue, it is crucial to update systems regularly and monitor for new vulnerabilities. Developing and rehearsing incident response protocols ensures rapid breach detection and mitigation.
Compliance audits help ensure systems adhere to relevant privacy laws. Employee training on cybersecurity best practices reduces the risk of unintentional human errors, leading to security breaches.
7. Combating Advanced Persistent Threats
To defend against APTs requires regular security assessments, encryption of sensitive data, participation in threat intelligence sharing, and adoption of a zero-trust security model. We can further secure our systems by utilizing advanced detection technologies, such as behavior-based threat detection systems, and preparing comprehensive incident response plans with forensic capabilities, which are effective measures.
8. Addressing the Cybersecurity Workforce Shortage
One of the most dangerous threats is that the cybersecurity workforce shortage has reached critical levels, with nearly 4 million unfilled positions globally. Organizations and governments must invest in cybersecurity education and training to bridge this gap and ensure robust defenses.
Many companies are adopting new technologies, conducting security audits, and hiring experienced professionals to strengthen their defenses.
Conclusion
To stay safe in the cybersecurity world of 2024, keeping up with new threats and having a solid plan to protect your data is crucial. By staying informed about the latest cybersecurity risks and methods used by attackers and employing strong security practices, organizations can better protect their information and remain resilient against the ever-changing landscape of cyber threats.
The Tech Junction is the ultimate hub for all things technology. Whether you’re a tech enthusiast or simply curious about the ever-evolving world of technology, this is your go-to portal.